Exploring Nmap, Interesting and Useful Flags
by Divya
Port Scanning opened new doors in my Networked Brain. Here’s few.
History
I recently completed the Nmap room on tryhackme. While this blog won’t be a walthrough(You’ll get many online), I planned to write this based on what new things I have learnt. How nmap works and how it send packets and receives different info on the target.
1. Interaction between you and the world
It’s easy for you to think the following:
- Client (You)
- Server (The place wherein sits the website you want to view)
The next part is easy, establish a connection, send a request. Server says “yep! here’s your website”. Simple.
But how?
Connections are made using ports. On your machine, there are several ports lying inactive saying “I need connection”. The server, on the other hand is sitting with a port open saying “I’m here! Connect with me!” Now you know every website you access, every connection you make outside your machine, everything is routed through each unallocated port on your machine. So it’s simply:
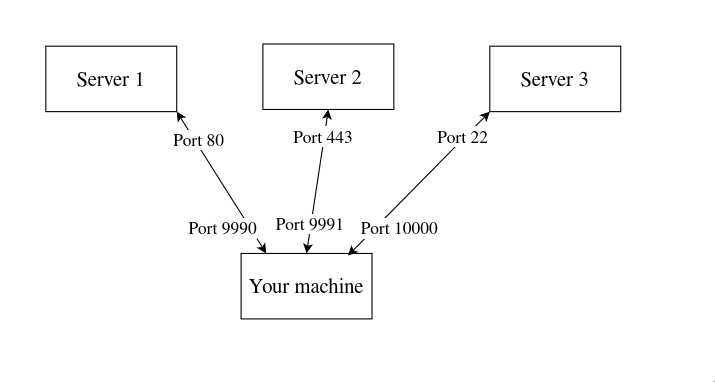
2. What constitutes each connection?
Each connection constitute packets. And each packet contains information about the sender port, the receiver port, data to be transmitted, etc. TCP (Transmission Control Protocol) is a reliable transport protocol as it establishes a connection before sending any data and everything that it sends is acknowledged by the receiver. Now we come to the structure of a basic TCP Packet.
- Source Port - Which port the packet originated from
- Destination Port - Which port the packet is entitled to reach
- Flags
- URG - Urgent Pointer, when 1, means it has urgent data
- ACK - Used for acknowledgment of the receival of a packet
- RST - Resets the connection, means to terminate the gateway
- PSH - Push flag, when 1, means to transmit the data immediately without waiting for the whole TCP segment
- SYN - Used during the 3 way handshake of a packet
- FIN - Finish flag, denotes the end of TCP connection
- Few more sections which are not needed to know basic working of nmap.
3. Types of Scans
TCP Scan -sT
The first basic scan comes is the TCP scan. This scan is used for the 3-way handshake rule. Nmap sends a packet with the syn flag set, the server responds with a packet that has the syn and ack flag set. And, finally nmap responds with an ack, denoting the host is up and working.
In case the host is down, it sends a packet with the rst flag set, thus reseting the connection.
Syn Scan -sS
Then comes the regular scan - the syn scan. Here, as tcp scan, nmap sends a syn packet to the server.
The target server sends a syn-ack saying “Yeah let’s connect!”
However in this case, nmap doesn’t send the ack that says “cool, here goes my connection”. It just drops the packet and goes away. Nmap now knows that the port on that server is open :)
it’s rightfully called as the Half Scan.
UDP Scan -sU
UDP connections, as we know are stateless. Here, there is no acknowledgment in response. Since there is no way to know whether port is open or not, it sends packet 2 times.
If by any chance, it receives a response, nmap marks the port as open. If no response comes whatsoever, it gets marked as open|filtered.
Due to this double checks and wait for response, udp scans are relatively slow. However, in case of a closed port, the target sens am ICMP(or ping) packet that contains the message saying the port is unreachable.
FIN Scan -sF
Here, nmap sends a packet with the FIN flag set(recall TCP header? NO? Go back). If the port is closed, the target responds with a packet with RST flag set.
NULL Scan -sN
Here, nmap sends packets with no flags set. Here as well, the target responds with a RST flag set request if port is closed.
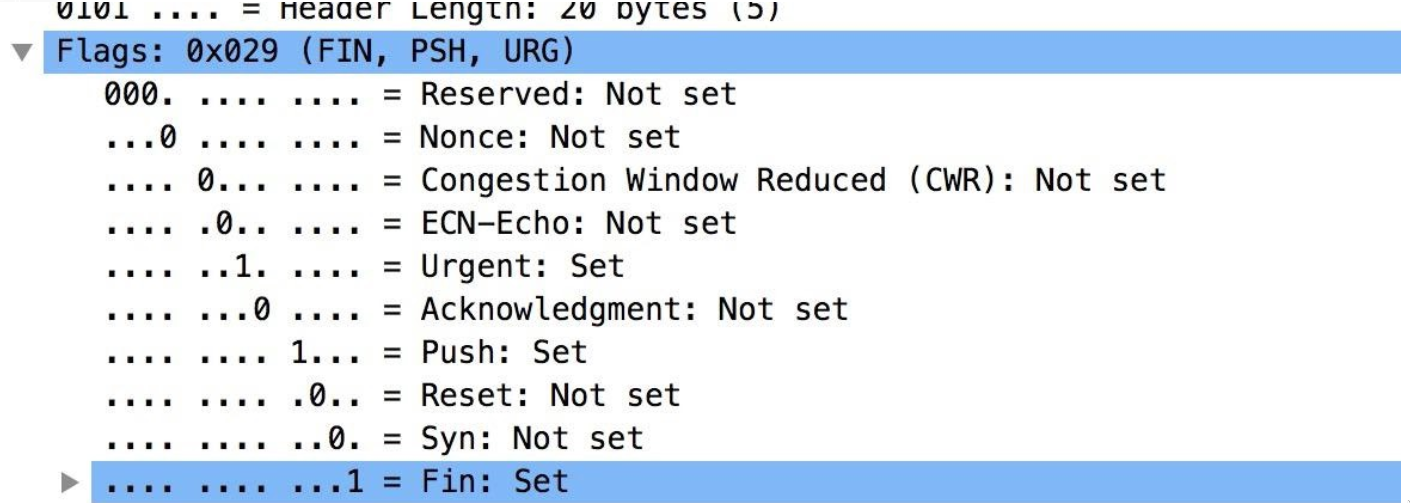
XMAS Scan -sX
Looks funny with the name? It is called XMAS because here, nmap sends a request with 3 flags set - PSH, URG and FIN. The structure of the header looks like an Xmas tree on Wireshark, thus giving the name. Here, as you can guess, the URG flag is set without any intended urgent data. Also, the PSH flag makes no sense here there is nothing to be transmitted immediately in the header. Thus, XMAS scan send malformed TCP packets to the target. If the target port is closed, it responds with an RST again.
4. Reason behind all the types. They get the same type of response back right?
Bypassing firewalls. Now think about this. We know every connection sends a syn for connection request. So, for a port that isn’t meant to make connections with the outer world can easily be configured to have a firewall set.
This firewall can be capable of dropping every packet that has the syn flag set. Each of the above scan types has different combination of flags and many firewalls aren’t that nicely configured to block each of them!
5. Let’s get our scans ordered.
For a user to start using nmap, it is crucial to know which hosts are up and running for us to enumerate. Thus, we ping a range of IP inside the network.
In this case, we can use -sn that “sweep”s through all the hosts inside the IP, pinging each and checking it’s activity. If yes, we move ahead scanning it’s ports.
If you want to scan all ports on a host, use -p-. This iterates through every port on the target and enumerates what service is running on each.
Running 2 VMs on my host and scanning them on nmap
6. Wait, there are scripts…
This is a section that can’t be covered in a single blog. Quoted from NSE(Nmap Scripting Engine)’s Documentation:
It allows users to write (and share) simple scripts to automate a wide variety of networking tasks. Those scripts are then executed in parallel with the speed and efficiency you expect from Nmap. Users can rely on the growing and diverse set of scripts distributed with Nmap, or write their own to meet custom needs.
Using the -sC which is equivalent to --script=default, you can utilise the already available scripts present with nmap on your machine.
With scripts, you can automate various tasks including vulnerability detection, network discovery and many more.
So that’s all I have to jot down for nmap! Found something more to discuss on nmap? Hit me up on twitter or mail!(Contact details below of page) For more read on’s, here’s some useful things I found:
[More Resources]
Structure of TCP Header
Nmap Scripting Engine
Tryhackme Nmap Room